History
First, we’ll take a quick trip down memory lane to revisit the history of IP addressing. We’ll touch on RFC 760 and how it initially defined IP addresses. Remember that back then, the first octet was reserved for the network, which only gave us a measly 256 networks. That wasn’t nearly enough.
Then came RFC 791 in 1981, which introduced classes—Class A, B, and C addresses. This improved things, but we were still limited to about 2 million networks. As the internet grew, we needed more networks and fewer addresses per network. This is where subnets enter the picture.
Subnetting and Borrowing Bits
Subnetting allows us to divide a network into smaller parts. Think of it as drawing a line in the sand within a Class A, B, or C address range. This line separates the network part from the host part. The trick is “borrowing” bits from the host part to create more networks. You can borrow one bit for two networks or eight bits for 256 networks. The location of that line is depending on what requirements your working with. The more bits you borrow, the more networks you’ll have, but also you will have less usable ip address for endpoints.
The example below shows a 10.0.0.0 network. The digital equivalent is displayed below it. We can tell by the first octet that this is a class A address. However, we can borrow 4 bits for the network bits. This is depicted by the yellow line
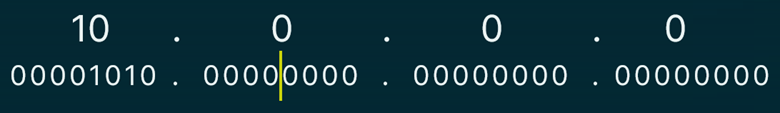
Drawing the line in the new location gives us 4 bits devoted to different networks. For every bit we add, we get twice the number of networks. To calculate how many networks we have created, raise 2 to the power of the number of bits we borrowed. In this case, we borrowed 4 bits. 2^4 power, which gives us 16 possibilities. We’ve just created 16 networks.
Note that the first 12 bits represent the network. However, we don’t include the first 8 bits when calculating how many networks we must work with. Typically, you will be assigned a network range that you are working with, or you are choosing from a private address range, a topic we’ll cover later. In this case, we have chosen the 10.0.0.0 network to work with, and are borrowing 4 more bits to create 16 networks out of that range.
