[et_pb_section fb_built=”1″ admin_label=”section” _builder_version=”4.25.1″ background_color=”#FFFFFF” border_color_all=”#052035″ global_colors_info=”{}” theme_builder_area=”post_content”][et_pb_row admin_label=”row” _builder_version=”4.25.1″ background_color=”#FFFFFF” background_size=”initial” background_position=”top_left” background_repeat=”repeat” global_colors_info=”{}” theme_builder_area=”post_content”][et_pb_column type=”4_4″ _builder_version=”4.16″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||” theme_builder_area=”post_content”][et_pb_text admin_label=”Text” _builder_version=”4.25.1″ text_text_color=”#000000″ background_color=”#FFFFFF” background_size=”initial” background_position=”top_left” background_repeat=”repeat” global_colors_info=”{}” theme_builder_area=”post_content” width=”100%”]
Though cryptography has existed for a considerable time, its importance has dramatically increased in modern times. The rise of global connectivity has led to an unprecedented demand for secure communication and data protection. Cryptography now serves as a linchpin in cybersecurity, crucial for shielding sensitive information from unauthorized access and malicious intent.
In this post, let’s explore the foundational concepts, principles, and cryptography terminology. This post lays the groundwork for what cryptography is at its core.
What is Cryptography?
In technical terms, cryptography refers to the practice and study of techniques for securing communication and data by encoding it in a manner that only authorized parties can access and understand. The term originates from the Greek words “Krypto,” meaning conceal or hidden, and “graphy,” referring to drawing, writing, or recording. Essentially, cryptography can be understood as the art and science of concealing and securing information through various methods of encoding and decoding. When it comes to Cybersecurity we can think of it as the art of concealing information.
Throughout this post, we will hide or conceal the word “secret”. We are concealing it into a code. In the below figure, we conceal the word SECRET as a coded message VHFUHW.
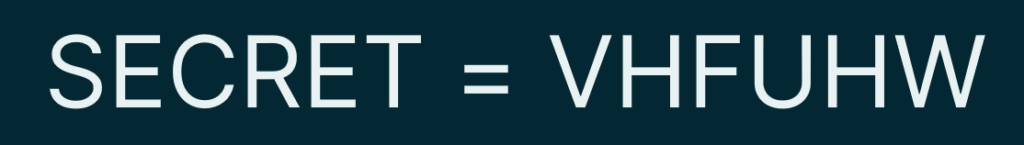
What is a Cryptographer?
A “cryptographer” refers to an individual tasked with either crafting or deciphering coded messages.
What is Plain Text?
“Plain text” denotes the original message before encryption. The figure below shows the portion that is considered to be plain text.

What is Cipher Text?
A “cipher text” represents the message after encryption. The yellow box in the figure below shows what we consider the cipher text.

What is Encryption?
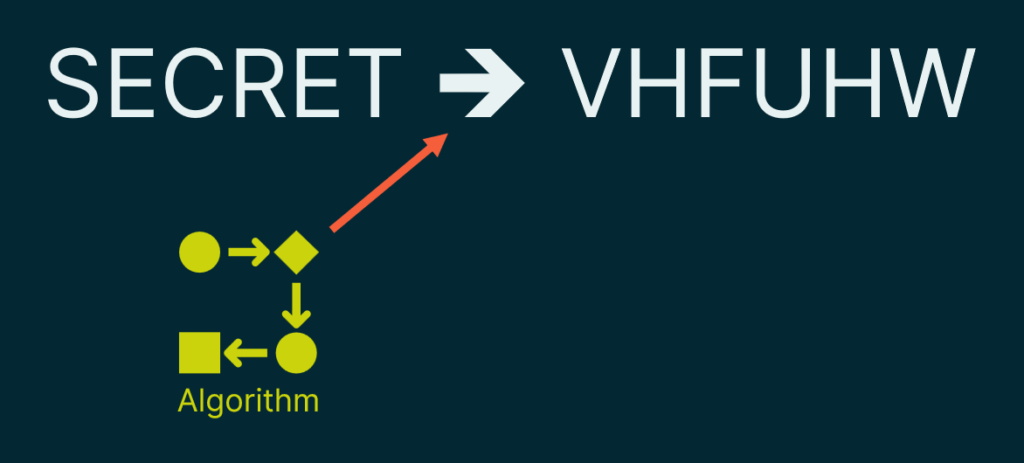
The process of transforming plain text into cipher text is termed “encryption.” In the figure below, the yellow box highlights the arrow which represents the process of turning plain text into cipher text.

What is Decryption?
Decryption is when we take the cipher text and convert it back to plain text. Notice in the figure below, that the arrow now is reversed. This denotes the process of reversing the encryption that happened in our last step.

What is a Cipher?
A cipher is just the process or algorithm that’s used to encrypt a message or decrypt a message. It is the process that it goes through, and there are a lot of different ciphers out there. AES, DES, and RSA are examples of ciphers that can be used to encrypt and decrypt messages.
Ciphers are a specific type of algorithm, the algorithms that are used to encrypt and decrypt messages.
What is an Algorithm?
In technical terms, an algorithm is a systematic procedure or set of instructions designed to solve a specific computational problem or perform a particular task. It involves taking an input, processing it through a defined sequence of steps, and producing an output. In essence, an algorithm encapsulates the logical and computational steps necessary to address a problem or achieve a desired result.
Example: here is the process defined in our cipher/algorithm:
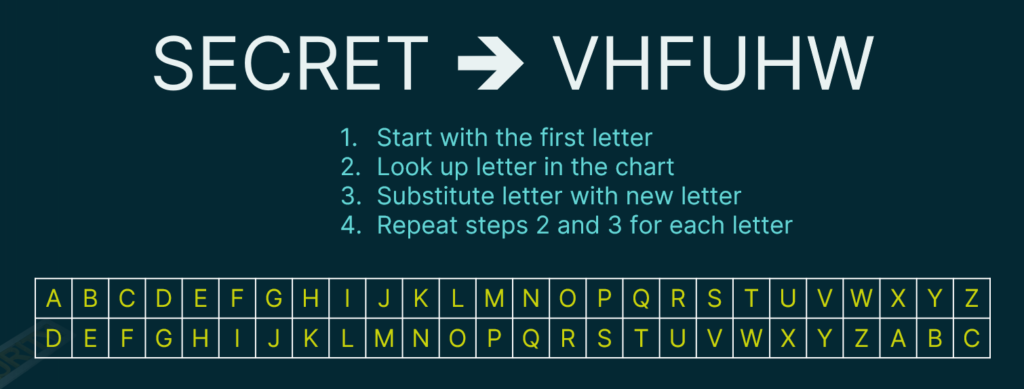
- Start with the first letter. Our first letter is S and we look it up on the chart.
- The corresponding letter to S is V in our chart. Substitute the letter with the new letter.
- Repeat steps one and two for each of the letters of the plain text. E becomes an H, C becomes an F, and so on.
SECRET = VHFUHW
| A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U | V | W | X | Y | Z |
| D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U | V | W | X | Y | Z | A | B | C |
This specific Cipher is known as the Ceasar Cipher because it was used by Julius Caesar around 58 BC, this is an old and simplistic way to encrypt and decrypt messages.
What is Cryptanalysis?
Cryptanalysis is the art of reverse engineering or decrypting things without knowing all the variables that go into it. In our example. Someone may figure out that our cipher text (VHFUHW) translates to SECRET when decoded without any table or prior knowledge of how it was encrypted to begin with.
A common trick to cryptanalysis is to look for repeated letters. The letter E is one of the most common letters in the English alphabet. If you see a repeated pattern, you could try substituting E’s for the most repeated letters. In our example, someone might guess that H’s has a high probability of being an E because of both the frequency of use and position in the cipher text. This assumption would be correct.
Someone may then try to create a decoding table shown above by shifting all letters to 3 positions. They could then use the table to decode the rest of the letters, which would also prove to be correct.
As you can see, this simple Caesar Cipher could be easily reverse-engineered, making it a poor cipher. We call this a weak cipher.
What is a Cipher Key?
A key is additional information that you need, along with the cipher, in order to encode or decode a secret message.
As you can see in our cryptanalysis description, a simple Caesar Cipher is easily discovered nowadays. We can make this a little more complex so it will be harder to break. For instance, maybe this time when you receive a message, it’s shifting the alphabet by 3 but maybe next time it’s going to be by 6, and maybe the time after that it’s going to be by 9. By shifting the letters a different amount every time, you’ve increased the complexity. Of course, you’ll need to know how many characters you need to shift the alphabet by, and that’s where the key comes into play.
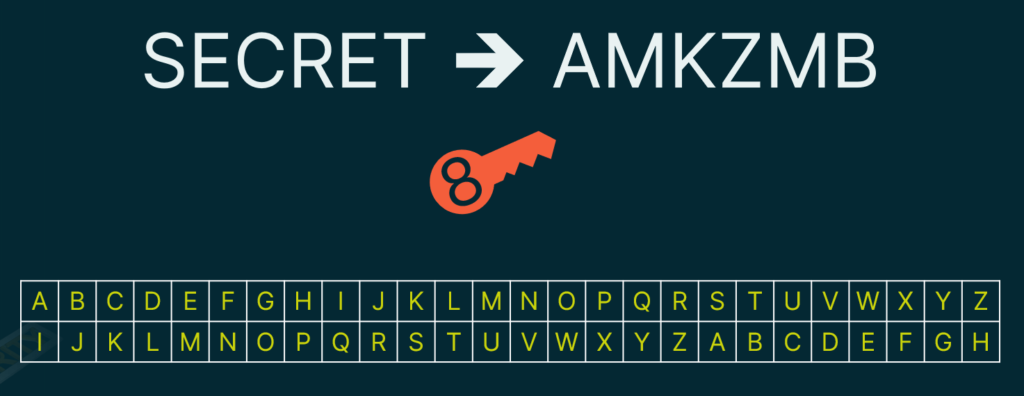
Essentially, a cipher key allows us to create more secure encryption even if someone knows the cipher that we are using. Modern cryptography requires the use of keys since the cipher algorithms are well-documented and known by many.
What is Substitution?
What we are doing here is a type of cryptography that is called substitution. We are substituting our letters for different letters. It doesn’t have to be other letters, it could be numbers, symbols, or other representations as well.
What is Transposition?
Transposition is another way that we can encrypt a message and we do that by shifting the letters rather than substituting them. Here is an example:
SECRET = ESRCTE

In the example, we’ve moved the 1st, 3rd, and 5th letters over one to create our cipher text.
Want to know more? Check our full module on encryption on our YouTube Channel:
Foundations of Cybersecurity, Module 6: Cryptography
We release new content often through our YouTube channel and our Newsletters.
Subscribe to our YouTube channel!
LinkedIn | Facebook | X | Instagram
[/et_pb_text][/et_pb_column][/et_pb_row][/et_pb_section]







